Last week on Wednesday 27 January, Afilias teamed up with the Joint Cyber Security Centre (JCSC) to facilitate a webinar on “Stopping Cybercriminals at the Internet Infrastructure Layer”. Alexander Falatovich, Senior Cyber Security Threat Analyst at Afilias led the presentation, sharing valuable insights from a registry perspective, as well as advice on what you need to know before reporting a cybercrime to a registry.
The threat landscape
To begin, Alex laid out the facts: cybercrime pays, which is why criminals do it. It costs businesses significant sums of money throughout the year, and unfortunately is not something that is going to slow down any time soon. He went on explaining that cyber attacks affect all types of organisations right across the world, noting an alarming statistic: a 350% increase in phishing attacks in the first quarter of 2020 as reported by the UN. He further stressed that recently, attacks have become much more sophisticated than ever seen before.
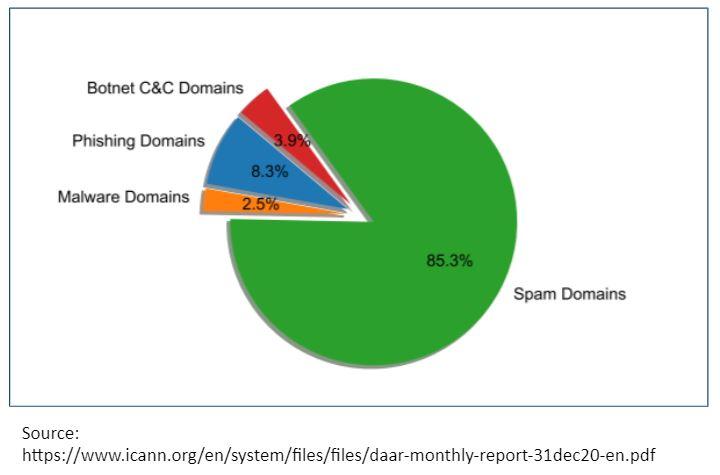
Alex revealed that domain names are used to perpetrate all kinds of crimes, from phishing to malware to botnet command & control attacks to spam domains. He showed us that spam domains make up the majority of abuse, using the below pie chart to highlight the impact:
The DNS ecosystem
When explaining how the DNS (Domain Name System) ecosystem works, Alex highlighted the role of two key coordinating and oversight bodies, The Internet Corporation for Assigned Names and Numbers (ICANN) and the Internet Assigned Numbers Authority (IANA). These organisations oversee the root of the internet, including the coordination of Top Level Domains (TLDs), including the .au TLD which is managed by our colleagues at .au Domain Administration (auDA), who set the policies for the .au namespace. Registrants and consumers can rest assured that the stringent eligibility criteria and policies in place to safeguard the .au namespace (as administered by auDA) makes it difficult for cybercriminals to operate, and ensures domain abuse remains well below the global average.
Alex highlighted that it is Afilias’ responsibility as Registry Services Provider for .au to ensure that policies set by auDA are observed. He further explained that since Afilias is connected to registrars like Crazy Domains (and not the public), it works closely with registrars on policy compliance issues.
Investigation & mitigation
When investigating cybercrime, Alex described a variety of internal and external tools and sources that are used for Domain Abuse Work at Afilias, many of which are also used by registrars and registrants in identifying cybercrime. He noted that Afilias uses in-house abuse management tools and DNS traffic data to identify potential threats:
“Our DNS nodes collect queries and the DNS traffic data which can provide insight around what domains are being queried, the volume in which they are being queried and this can be useful for things such as identifying a DDoS (Distributed Denial of Service) attack or looking to see about specific domains that may look suspicious...”.
If a domain appears to have been registered for the purpose of cybercrime, Afilias will send a notice to the sponsoring registrar. The registrar will then work with Afilias to apply a lock to the domain name (i.e. stop it from working) so that it can no longer be accessed by an unsuspecting end user.
Alex stressed that although registries and registrars are not law enforcement bodies, we have clear policies that prohibit illicit use of domain names and we actively enforce these policies in order to protect the public. If you want to reach out directly to a registry to report a crime, ensure you have your evidence together (such as a screenshot and/or URL of the applicable domain) and understand the policies relevant to that particular registry. Finally, Alex reminded us that we are all looking to achieve the same goal, to reduce cybercrime, and this is what needs to remain front of mind as we continue to fight the battle together.
Have a question, comment or idea for a future blog post? Email us at blog@afilias.com.au today.